Simple Tips About How To Detect Conficker Infection
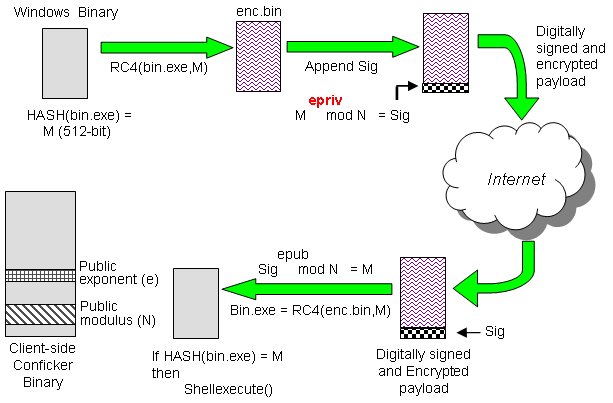
The latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139 and port 445.
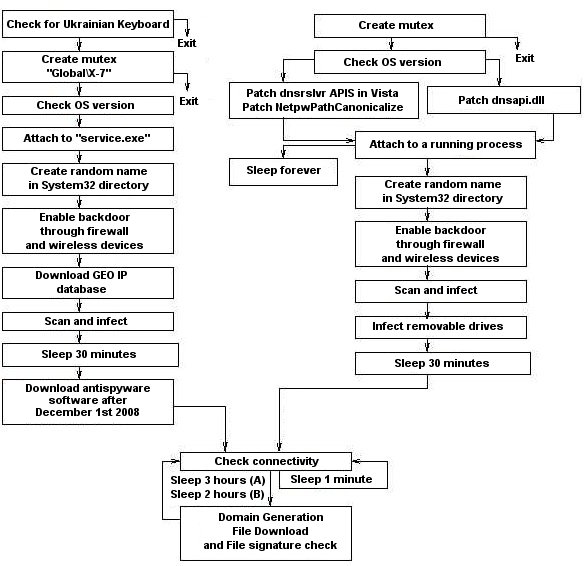
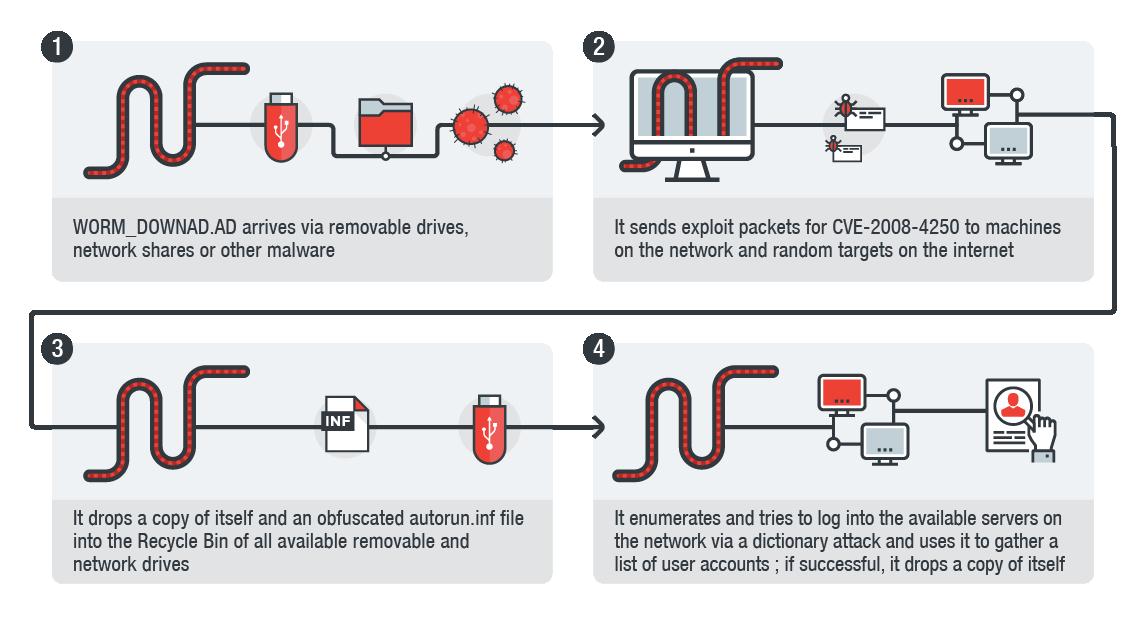
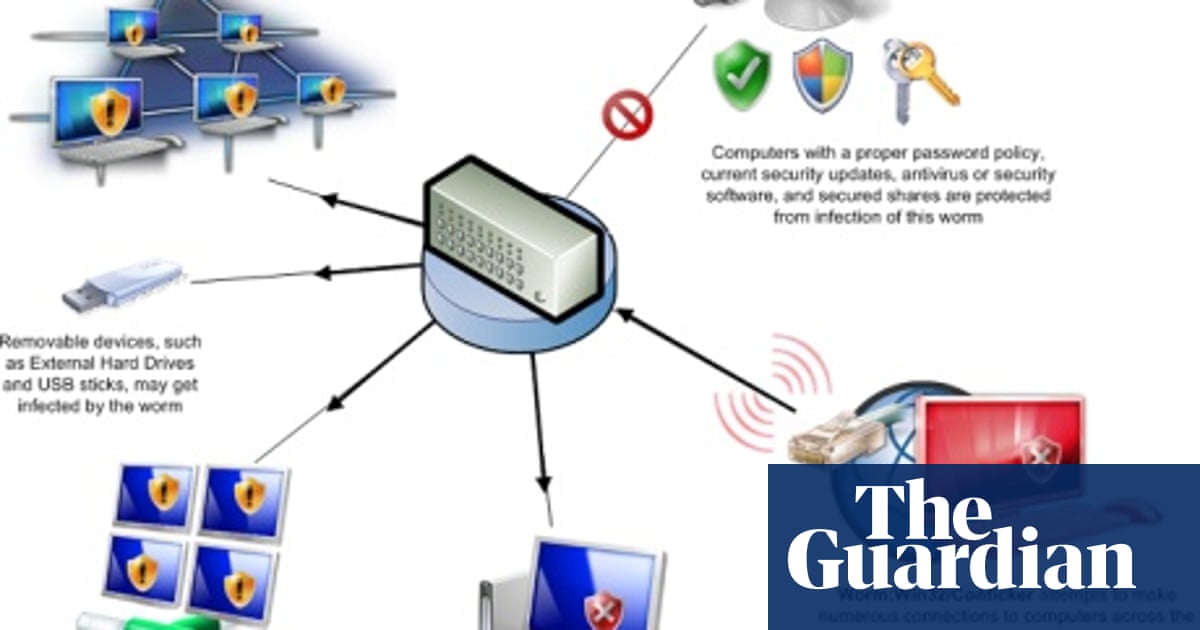
How to detect conficker infection. Even though more than 15 million ( some are saying more than 20 million) computers are infected, they are still saying it's not that bad, but trust me. Symptoms of a conficker infection include: If you fear you have an infection, you can download sophos’s free conficker removal tool, which detects, isolates, and removes conficker from your computer or network.
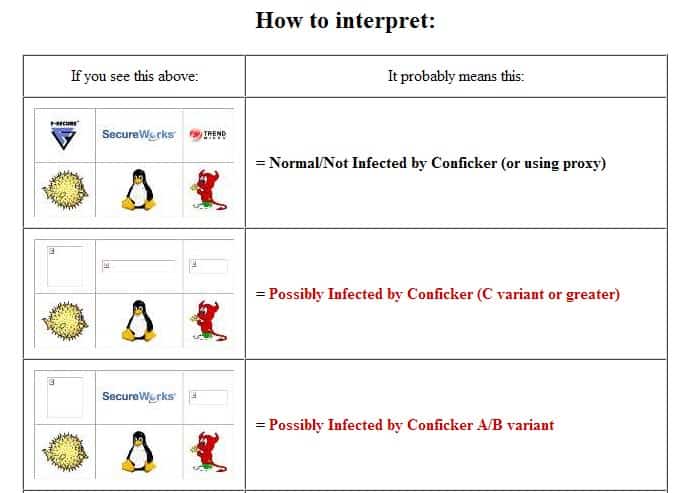
The group’s “ conficker eye chart ” pulls images from three sites that conficker is known to block and displays them in a box. March 30, 2009 | 1 min read nessus plugin # 36036 performs a network based check for windows computers infected with a variant of the conficker virus. A windows python to exe build of the same tool is available.
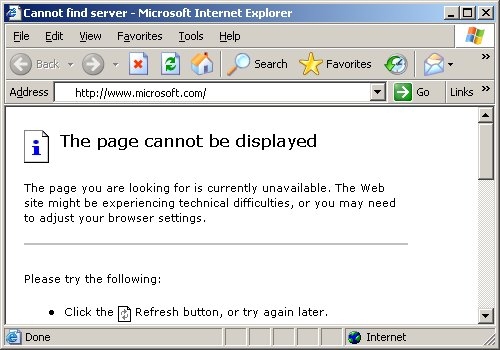
If, on the other hand, any of the images are. All you do is head to the conficker eye chart and check the table at the top. The presence of an infection may be detected if users are unable to connect to their security solution web site or if they are unable to download free detection/removal tools.
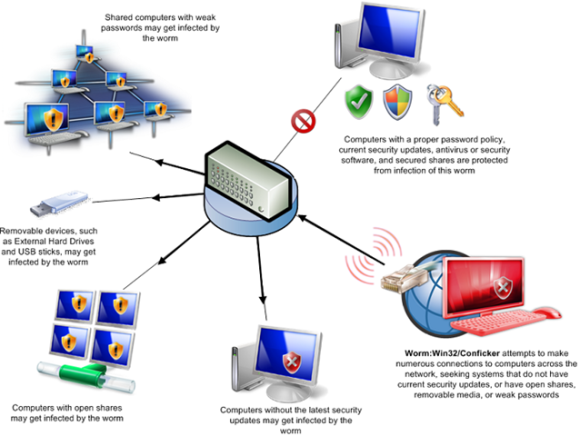
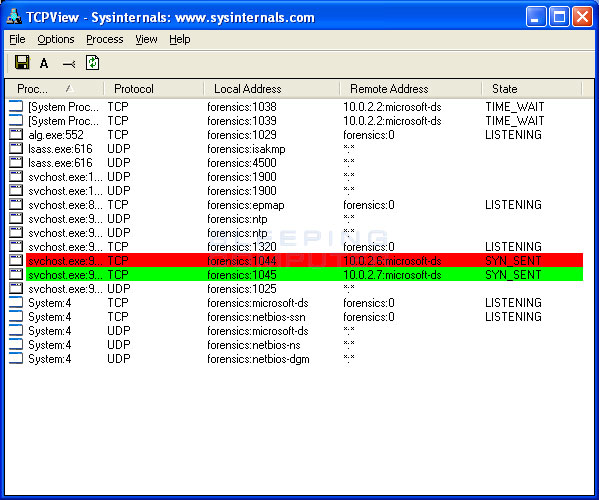
Below the box is a guide to interpreting how you. If you suspect that a conficker infection is in place on computers in your network, you can use the free utility nmap to detect infected clients using the following commands: It compromised computers for business, government, and home uses across the world.
If you choose not to. 127.99.100.2 seems to be infected by conficker./scs.py 127.36.15.80 127.36.15.80 seems to be clean. Use the following free microsoft software to detect and remove this threat:
Account lockout policies being reset automatically. If you see all six images, you're golden:




/cloudfront-us-east-1.images.arcpublishing.com/gray/H625APTEBJCF7C5NR4PHG25M7A.jpg)